Identity and Access Management (IAM) is instrumental in securing cloud environments.
By default, Amazon Web Services’ (AWS) IAM Service provides a minimal password policy that does not meet industry security standards.
To strengthen authentication controls, aligning IAM with the Center for Internet Security (CIS) AWS Foundations Benchmark v1.2 is necessary.
This short post will show you how to ensure that all current and future users in your AWS account create strong passwords.
Default AWS IAM Password Policy
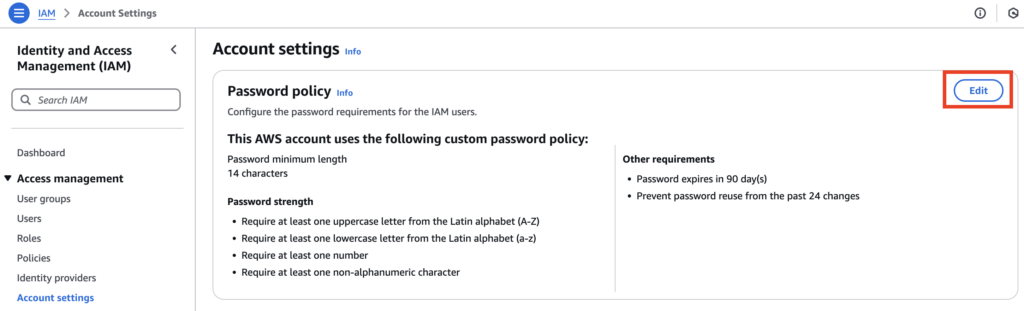
Figure 1. By navigating to AWS IAM Service under Account Settings, you will see that AWS’ default password policy is weak. Select Edit to adjust your password policy.
Configuring a CIS-Compliant Password Policy
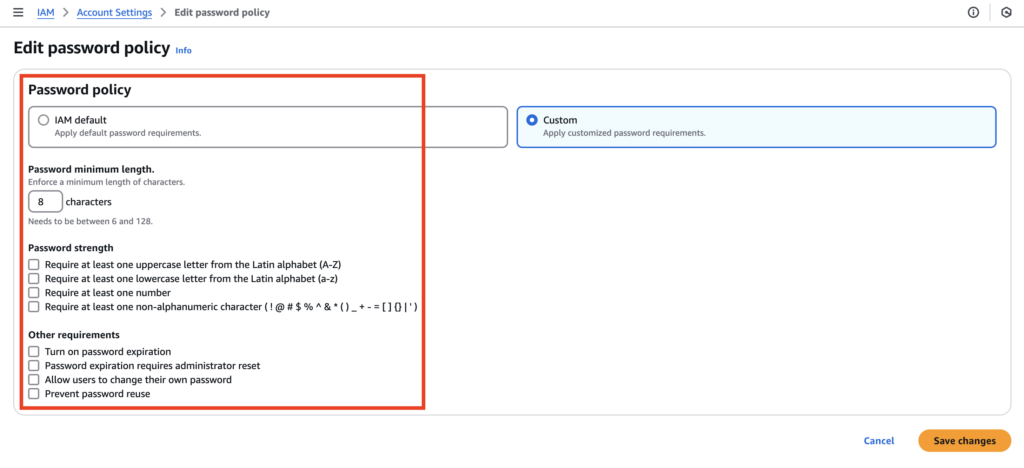
Figure 2. IAM default is selected by default, select Custom. You are now ready to configure your default password policy using the CIS Benchmarks.
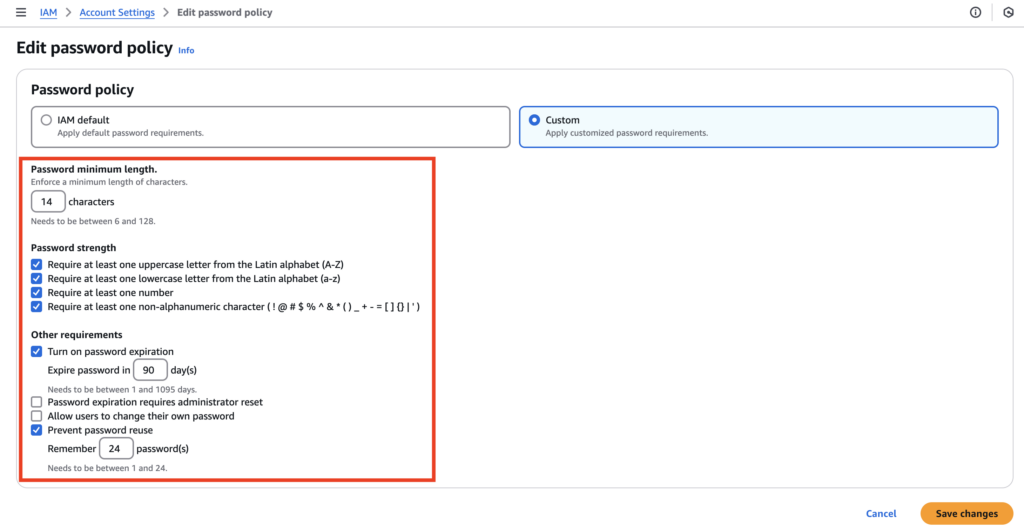
Figure 3. The screenshot above shows the configured password policy aligned with CIS AWS Foundations Benchmark v1.2, implementing Controls 1.5–1.11.
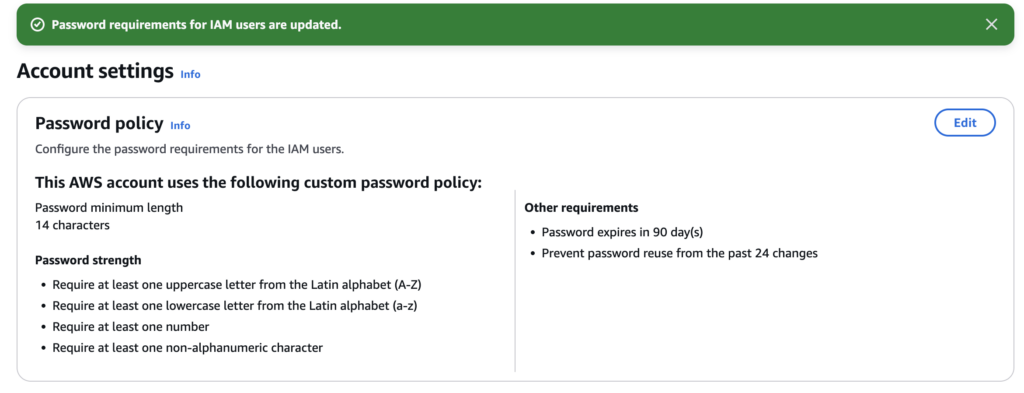
Figure 4. After selecting Save Changes, you will receive confirmation that your new password requirements, implementing the IAM-related CIS Controls, have been successfully updated to reflect your newly configured policy.
Final Thoughts: IAM is the New Perimeter
Weak password policies leave accounts vulnerable. The default AWS policy isn’t enough—enforcing CIS controls strengthens security by requiring strong passwords, expiration, and reuse prevention. Securing IAM is essential to protecting your AWS environment.


